A security researcher, James Fisher, details a new phishing attack on Chrome on smartphone: the trick is to create a false address bar that replaces the browser. Authentic in appearance, this bar, nicknamed "Inception" by its creator, ensures the visitor that he is on the right page, and enjoys a secure connection. It can also trap it in an environment controlled by hackers, even when it tries to leave the page.
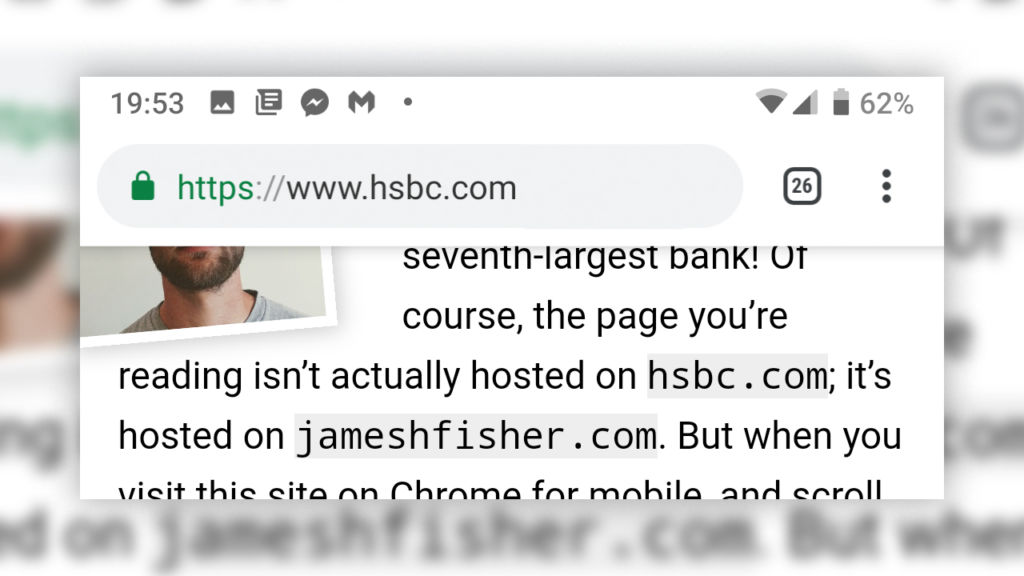
A developer, James Fisher, details on his site a new type of phishing attack. Called "Inception", the exploit reproduces the appearance of an authentic page on a smartphone using a simple capture of an address bar obtained during a visit to a site - in this case the one from HSBC.com. He explains in his article how to push the concept in its limits, and thus trap the visitor in a kind of navigator nested in Chrome.
We learn that Chrome for Android can allow a developer to completely substitute the graphic element of the address bar with another, manufactured from A to Z by hackers. It details how to prevent, for example, that the real search bar appears when the user scrolls the screen. Or replace this address bar - which may be a simple image - by a real field in which the user can enter any address of his choice.
The hackers will then have the opportunity to spy on what the user does on other sites, or even aspire his identifiers en route. This attack is surprisingly difficult to spot, and that seems to make it very dangerous. The researcher suggests Google engineers force a graphical element to be displayed that prevents the page from being able to display whatever it wants on the entire screen. An element that could signal that the real address bar is hidden, and allow the user to make it reappear by touching the message.
Chrome: new phishing attack via an address bar worthy of "Inception"
We learn that Chrome for Android can allow a developer to completely substitute the graphic element of the address bar with another, manufactured from A to Z by hackers. It details how to prevent, for example, that the real search bar appears when the user scrolls the screen. Or replace this address bar - which may be a simple image - by a real field in which the user can enter any address of his choice.
The hackers will then have the opportunity to spy on what the user does on other sites, or even aspire his identifiers en route. This attack is surprisingly difficult to spot, and that seems to make it very dangerous. The researcher suggests Google engineers force a graphical element to be displayed that prevents the page from being able to display whatever it wants on the entire screen. An element that could signal that the real address bar is hidden, and allow the user to make it reappear by touching the message.

