Kaspersky reveals that hackers have managed to infect Asus' servers and push a malware on 57,000 PCs by imitating the manufacturer's digital certificates. The attack was aimed at Live Update, a program supposed to automate Asus software updates, and to update the BIOS on compatible motherboards. Kaspersky explains: "A legitimate certificate was used to sign the tool used as a Trojan, and it was hosted on the official ASUS server specifically created for updates. This method allowed him to go unnoticed for a while. The criminals also made sure that the size of the malware was the same as the original program. "
Asus Live Update has infected thousands of PCs with malware unbeknownst to users
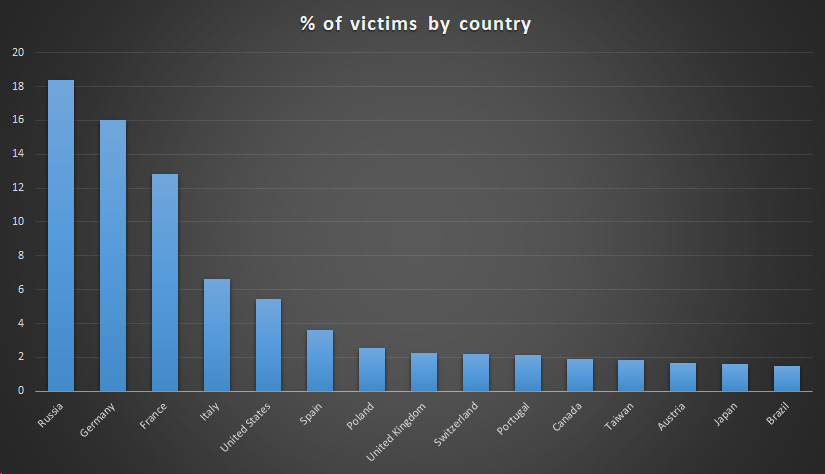
Kaspersky explains that hackers were not interested in everyone: "they only targeted 600 MAC addresses in particular." The firm's statistics show that the main countries affected are Russia, Germany and France. ShadowHammer is the name given to this very complex and sophisticated "supply chain" attack. His analysis is still going on to find out exactly what the hackers were trying to steal. Anyway, Kaspersky says he discovered the problem in January 2019 and immediately notified Asus. At first, Kaspersky regretted that Asus remained "largely insensitive [to his report] and did not inform customers of the problem".
Since then, however, Asus seems to have caught up at startup: "Our ASUS customer service has contacted affected users to help them eliminate any potential security risks. In addition, ASUS has corrected the latest version of the Live Update software (ver 3.6.8), introducing in particular multiple security verification mechanisms that prevent any malicious manipulation in the form of software updates or other ", explains the company. a statement. If you use Asus products, it is strongly recommended that you upgrade to Live Update 3.6.8 as soon as possible and perform an antivirus scan.